|
|
“You can fool some of the people all of the time, and all of the people some of the time,
but you can not fool all of the people all of the time.”
-Abraham Lincoln
What is ARP spoofing, and why do I care? If you’re old enough, you might remember the TV show “To Tell The Truth.” The show features a panel of four celebrities attempting to correctly identify a described contestant who has an unusual occupation or experience. This central character is accompanied by two impostors who pretend to be the central character. The celebrity panelists question the three contestants; the impostors are allowed to lie but the central character is sworn “to tell the truth”. After questioning, the panel attempts to identify which of the three challengers is telling the truth and is thus the central character.
Your computer is like one of the celebrities in “To Tell The Truth”. To communicate on your home network, your computer needs to know how to talk to your wireless router. So, it broadcasts a question on your network: “Hey, router: Where you you?”. In computerese, the question looks like: “Who has IP address 192.168.1.1. Tell 192.168.1.11”. In Wireshark, it looks like this:

After your computer broadcasts the question, it listens for an answer. Normally, your wireless router will answer “Here I am!!”. In computerese, the answer looks like “192.168.1.1 is at 28:c6:8e:a4:3c:71”.
In a way, this is a little bit like “To Tell The Truth”. Pretend you are one of the celebrities. There is a mystery guest, and two imposters. The mystery guest is Abe Lincoln, and both imposters are dressed up to look like Abe Lincoln. They all have beards, and a tall stove-pipe hat. Their voices are all the same. How would you tell the real Abe Lincoln from the imposters? You would ask probing questions, right?
For your computer, it is actually harder to tell. Your computer can’t see the contestants. It can’t ask any probing questions. The only thing your computer can ask is: Which one of you is Abe Lincoln? Now, under normal circumstances, only the real Abe Lincoln will answer “I am the real Abe Lincoln”. And, you would begin a conversation with one of the greatest presidents the USA has ever had.
However, if there is a hacker on your network, they can also answer “I am the real Abe Lincoln”. The unfortunate part is that your computer can’t verify identities, so it just has to assume that the conversation it is beginning to have is with the real Abe Lincoln. That is what ARP spoofing is all about. It is getting your computer to talk to the hackers computer, instead of to your wireless router.
Suppose you now browse to your bank’s website. The hacker can forward your browser traffic to the bank’s website, and become a “Man In The Middle”, someone between you and your bank. This sort of attack is called a “Man In The Middle” attack. Using a program called SSL Strip, the hacker can intercept and decode your SSL traffic, then forward your browser requests to your REAL bank. Or, if you are shopping, the hacker can send it to Amazon.com, etc. (SSL Strip doesn’t actually decode the SSL traffic, but the net effect is the same.) Once the hacker intercepts your credit card number or bank account information, you’re in real trouble.
What can you do to prevent this? The SSL Strip program starts with an ARP spoofing attack, so let’s make ARP spoofing harder. How do we do that? There is a good webpage that talks about his very thing: “HOWTO : Protect you from being ARP spoofing.” It also has links to videos that show how to do these attacks (lovely). The author, Samiux, has some good pointers for avoiding ARP spoofing. For Windows and Linux, he points you to “XArp – Advanced ARP Spoofing Detection.”
The author of XArp is Dr. Christoph P. Mayer. His presentation “Securing ARP: An overview of threats, approaches, and solutions” is the most thorough analysis I have seen related to ARP spoofing. Dr. Mayer has a very comprehensive description of what ARP spoofing is, the various types of ARP spoofing, a large number of possible techniques to combat it, strengths and weaknesses of the individual techniques, and a suggestion that you obtain his program XArp. On his website, you can download a free version of XArp (fewer features) or you can buy XArp Professional (more features).
Another research paper on this topic is: “Securing Wireless Networks from ARP Cache Poisoning,” by Roney Philip, San Jose State University. Roney actually writes wireless router firmware to protect against ARP spoofing.
Cicso has a very good paper, “ARP Poisoning Attack and Mitigation Techniques,” that describes two security features of the Cisco Catalyst 6500 Series Switches: DHCP Snooping and Dynamic ARP Inspection (DAI). I don’t know if you have to turn them on or if they are automatically enabled.
Symantec Endpoint Protection, an enterprise-class security suite, has an option to protect against ARP spoofing, but you have to turn it on:

What to do:
1) Make sure your wireless router is configured to support WPA2-AES, and that you have a very strong password.
2) Review the webpage “HOWTO : Protect you from being ARP spoofing” for programs you can install that will help protect against ARP spoofing.
3) If you’re connected to a public wireless network, don’t do any online banking, or make any online purchases. The public network you are connecting to might be a hackers laptop.
4) At your office, refer your network administrators to this page. They probably already know all this (and more), but it will serve as a gentle reminder that protection doesn’t do you any good if you don’t turn it on.
What is a security sandbox? Think about the type of sandbox that kids play in. It is small, safe environment where kids can play with just the toys in the sandbox, and they’re temporarily contained so that they can’t touch anything outside the sandbox (unless they leave the sandbox).

In computer security, there is a concept called the principle of least privilege. What this means is that, when you run a program, it is only given the privileges that it needs to do its job, and no more. For example, Quicken doesn’t need to read your recipe file, and your cooking program doesn’t need to read your Quicken file. This is important. Why? Because if you download a cooking program, because it looks useful and innocent, but is actually malicious, it could send all your files to HACKERS_R_US.COM. We certainly don’t want that. So, we need to implement the principle of least privilege.
How can we keep our possible malicious programs from accessing our Quicken file? Let me stretch the sandbox analogy a little more. Let’s say that the things in the sandbox are files that our program can access, and let’s say that the little kiddo is our program.
Let’s create two separate security sandboxes. One sandbox will be for Quicken, and the other sandbox will be for our example malicious program.
 
There are two different sandboxes. The files in one sandbox can only be accessed by the program that runs in that sandbox. If a program runs in a different sandbox, then it can’t see files outside of its own sandbox.
That, in a nutshell, is what a security sandbox is. It is just a “box” that a program can run it, that limits what that program can see and do. It is a way to implement the principle of least privilege.
Another way to look at it: The Mac OS X Developer Library has a webpage called About App Sandbox. It’s a pretty helpful diagram:

On the left-hand side, when you run your app without a sandbox, it can access all system resources and all user data on your computer. On the right-hand side, when you run your app in a sandbox, it can only access the resource and user data that it is supposed to access, and no more.
This is great, right? Well, it would be great, except that in Windows 8 and Mac OS X Mountain Lion (10.8) or later, the sandboxes are voluntary. On the right-hand side, you have an app that can only play in their own sandbox. On the left-hand side, you have an app that can play outside the sandboxes, and also inside ALL the sandboxes.
Programs running outside of a sandbox defeat all the security measures that we were trying to put into place by implementing sandboxes in the first place. This is a side-effect of the basic security model of Windows, Mac OS X, and Linux that opens everyone up to security threats.
To learn more about security sandboxes, read:
A few months ago, I had a problem with one of my Virtual Machines (VMs), so I fired up Wireshark, and started capturing traffic. At first I thought I was seeing things. There was a bunch of traffic that was not originating on the VM; it was originating on the host OS. That seemed mighty odd. So I did some research.
Apparently, in a Windows VM, you can put the NIC into promiscuous mode, and you can see network traffic on the host. Not only that, you can see network traffic originating on other VMs! Bill Claybrook, a contributor to SearchVMWare, explains the purpose of promiscuous mode:
Promiscuous mode allows a virtual network device — such as a network adapter or virtual network interface card (vNIC) — to intercept and access data in a virtual network packet, including packets intended for other vNICs. If promiscuous mode is disabled, a vNIC will normally drop a packet that’s addressed to a different MAC address. Not all hypervisors allow promiscuous mode (e.g., Microsoft Hyper-V), while other do, such as VMware vSphere.
Claybrook goes on to suggest that you disable promiscuous mode from all your virtual servers. But that’s easier said than done. In fact, for the VMware Workstation (VMware’s hosted virtualization solution), running on Windows, the network adapters have promiscuous mode set on, and you can’t change it.
I’m not the only one having this problem. One user in a support community writes:
“And yes it seems in Workstation for PC promiscuous mode is permanently switched on. And that there is no way to switch it off! I wonder how this effects security?”
The answer is that it compromises your system’s security. A Virtual Machine is not quite the isolated security sandboxthat I thought it was. Edward Haletky, another contributor for SearchVMWare, concludes that– because some systems require promiscuous mode, and because the mitigation steps aren’t foolproof– the best thing to do is implement a rigorous auditing process and strong firewalls:
“Nothing can replace auditing changes to your infrastructure on a regular basis. Several companies have products that do this: Tripwire and Configuresoft. Other companies have tools to prevent traffic to and from the VM in question by placing a virtual jail around the VM: Catbird and Reflex Security… No matter which tool you choose, the use of promiscuous mode enabled port groups implies the need to increase auditing and your own diligent observations.”
Yesterday, I was wondering why my PC was getting logs of these NetBOIS Name queries to WPAD:

Turns out that WPAD is one of Internet Explorer’s worst features. It’s just one of those stupid little things that may be turned on by default that leaves your PC open to hackers.
What can you do to protect yourself? Go into your browser settings and disable proxy autodetection. It will even help your web pages open quicker– a win-win situation!
For more on browser security, read:
Software is a fact of modern life, but not all of it is safe to use. The real problem is that there is no way for us to tell if a program is good or not. There is no software vetting process, no “seal of approval” that our programs are good, so all we can do is trust and hope that the programs we run on our computers are good. There are three strikes against us:
- All programs have defects (bugs). If a vendor tells you their software doesn’t have defects, they are ignorant or lying.
- Most programs will do some things that, if you were told they did it, you would question why they needed to do it (data collection, advertising, etc.)
- A small percentage of programs are intentionally deceptive and malicious, causing damage, stealing data, stealing passwords, attempting fraud, etc.
If we run a program when we are logged in as “John Smith”, we are hoping that:
- The software defects aren’t bad enough to hurt us.
- The data collection won’t jeopardize our privacy, and the advertising won’t be too annoying.
- The program isn’t intentionally deceptive and malicious.
That is true most of the time, but not all of the time. And, when we run a program when we are logged in as “John Smith”, it has FULL CONTROL of ALL of our data files.
Because of this, we really need all programs to run in a security sandbox. The sandbox needs to be big enough so programs can do what is reasonable that they should do, but small enough to protect the confidentiality and integrity of our data (more relevant concepts here: http://en.wikipedia.org/wiki/Information_security). Certainly, the sandbox needs to be small enough so the programs can’t do any damage.
Joanna Rutkowska, someone much more knowledgeable about this than I am, has come to the same conclusion.
To learn more about security sandboxes, check out:
By now, I hope you’re aware that all of your programs can access your Quicken data. If you don’t care if your data is lost, destroyed, stolen, or published on the Internet, then you don’t have anything to worry about. For the rest of us, it’s an issue that needs to be addressed immediately. Here’s what you can do:
- If you think this information is important, tell your friends.
- Implement security sandboxes. (Learn what a security sandbox is.)
- Another potential solution is to run different programs as separate users. Still researching this. Will let you know what I find out.
- Review the data protection laws that govern your region. If you have any data protected by those laws, make sure the data is protected. It would be safer to move the protected data off PC and Macs completely, and onto servers inside your organization. In the US, some examples would be:
- any data protected by HIPAA
- any Personally Identifiable Information
- any data protected by security breach notification laws
- any data that could be used for identity theft
- If you have any personal data that you want to keep private (financial data, business plans, correspondence, etc.), the only way to guarantee that the data won’t be leaked to the Internet by a rouge program is to disconnect the PC or Mac from the Internet.
My wife and daughter use Macs, so I need to be at least somewhat aware of Mac security. The general consensus is that Mac security is better than Microsoft… but that’s a pretty low bar. How vulnerable are Macs?
I’m tired of hearing from Mac people how secure Mac OS X is. Apparently, I’m not the only one. An anonymous blogger has written a blistering, well-documented article about Max OS X security. The take-away? Don’t assume that Mac OS X is more secure than Windows. More hackers target Windows because it is a bigger target. But Mac OS X has its own vulnerabilities and is not immune to hacking attacks.
Kaspersky Lab is a leading provider of security software. Kaspersky’s chief technology officer Nikolai Grebennikov has said that “Mac OS is really vulnerable.” Kaspersky founder and CEO Eugene Kaspersky commented on Apple security: “I think they [Apple] are ten years behind Microsoft in terms of security.” Sure, they have something to gain by scaring people into buying antivirus software. But they are also experts in this field.
So, what can you do to protect yourself from hackers? Many Mac users chose the operating system because they want something that’s easier to use, and they like the idea of single package that contains everything they need for home computing. Naturally, these users balk at installing extra security software. (My daughter especially!) So, for those who just want to keep things simple, here’s a user-friendly guide to computer security for Mac users. For those of you who are feeling ambitious, check out the Mac OS X Security Configuration Guides published by Apple.
Hacking attacks happen all the time and pose a real security threat. Here are ten things you can do to protect yourself:
1) Don’t use the same password for all of your user accounts. Choose a variety of passwords, and make each one strong (no full words, use both numbers and letters). Keep your list of passwords in a safe place– NOT on your computer!
2) Don’t share personal information on any website unless you have a secure connection (i.e. the url starts with https). Log out of all personal accounts at the end of each session.
3) Install firewalls.
4) Update your machine and software to take advantage of new security sandbox technology.
5) Don’t run free software downloads unless you trust the source.
6) Strengthen the security of your home wifi network by using a WPA-2 protection protocol.
7) Install software updates when they become available– many contain patches that improve your software’s security.
8) Keep abreast of current security issues:
- For Windows PCs: Subscribe to: http://www.microsoft.com/security/resources/newsletter.aspx. Microsoft is a leader in the security field, in many respects. They have to be; they are the biggest target.
- For Macs: Scheduling regular software updates through System Preferences. If you really want to beef up on security for your Mac, check out the Mac OS X Security Configuration Guides published by Apple. Unfortunately, the newest guide is for Snow Leopard (10.6). Some guides for older versions of Max OS X are missing; the links are dead. You can find the Tiger (10.4) guide still on the NSA site.
- For Linux: Each Linux distribution will have its own website. Check that website for security information.
9) Be hyper-vigilant if you provide Internet content (for ANY website, including WordPress websites). After hearing the story of a friend of mine who runs a WordPress site, I realized that if you’re not careful, you can be held for ransom by hackers who threaten your website.
- If you’re not doing it already, make the Internet Storm Center part of your normal daily reading. These folks are GREAT! Their business is computer security education, and they have lots of great classes on various computer security topics. The Internet Storm Center website has the latest news about the hacking going on on the Internet. It’s one of the best computer security websites I know of.
- If you’re not doing it already, go to SecurityFocus and subscribe to the Bugtraq mailing list. You will get email about software vulnerabilities and updates. The notifications include information about WordPress and WordPress plugins. It’s a fairly active list. If you see a vulnerability for a software package you are running, you should research it, and see if there is a workaround you can implement. If you see an update for a software package that you are running, you need to apply the update ASAP.
10) If you’re still nervous (or if, like me, you’re really interested in this stuff), do more research! Here are some resources:
You may not know it, but ALL your programs can access your Quicken data. Not good. So, what can you do?
One solution to this nasty problem is to run all programs in a security sandbox. Unfortunately, the sandboxes in Windows 8 and Mac OS X Mountain Lion (10.8) are voluntary. Programmers can choose to use the sandbox security model, or they can choose to use the original user-based security model. All that it takes to subvert the new sandboxes is to install a program that is written for the old security model.
McAfee has some very interesting articles about the Windows 8 sandbox.
1) https://blogs.mcafee.com/mcafee-labs/windows-8-metro-brings-new-security-risks
2) https://blogs.mcafee.com/mcafee-labs/metro-interface-improves-windows-8-while-increasing-some-risks
3) http://blogs.mcafee.com/mcafee-labs/stronger-windows-8-still-vulnerable-through-apps-users This blog has one comment that I find really interesting:
“With Windows 8, desktop and Metro applications coexist to maintain backward compatibility with current Windows desktop applications. Windows also allows desktop applications to be installed and executed outside the usual constraints of Metro applications. This presents an interesting situation: Metro apps cannot get out of their sandbox; but desktop apps can enter the sandbox.”
What does this mean? It means that participation in the Metro sandbox security mechanism is voluntary, and that desktop apps don’t play by those rules. So, the Windows 8 sandbox is really easy to subvert – just install a desktop app. So, if you’re counting on sandboxes to keep your information secure, be careful what software you run! [INTERNAL LINK]
Here’s how to implement a security sandbox:
a) For Apple iPads and iPhones: these devices are running iOS, and all programs run in a sandbox. So, you don’t need to worry (as much) about those devices.
b) For Windows, you’re going to need to buy all new software, so you might as well buy a new PC. It must be running Windows 8 or later. Once you have done that, purchase and run only programs that are available from the Windows App store. If you’re not happy with that alternative, let Microsoft know. But, from a security perspective, it looks like they are doing the right thing.
c) For Mac OS X, you’re going to need to buy all new software, so you might as well buy a new Mac OS X computer. It must be running Mac OS X Mountain Lion (10.8) or later. Once you have done that, purchase and run only programs that are available from the Apple App store, or are deemed acceptable by Gatekeeper . If you’re not happy with that alternative, let Apple know. But, from a security perspective, it looks like they are doing the right thing.
I heard from a friend of mine, Paul Adams, who is very knowledgeable about Apple products: His comments:
a) All apps purchased through the app store for Mac OS X are sandboxed. It’s a requirement for developers who submit apps to the store to support it.
b) Look at the “gatekeeper” in Mac OS X 10.8 as well. It checks apps you install from the internet and will only let you run apps from “Trusted Developers” (an online list maintained by Apple), it’s a medium type setting for people who don’t want to be restricted to only the app store downloads but want to have some restrictions from the free-wheeling internet.
To learn more about security sandboxes, check out:
Note: The issue discussed on this page affects you if you use Windows or Mac OS X, unless you have taken the following precautions:
- For Windows: You are running Windows 8 or later, and only purchase and run programs from the Windows App store.
- For Mac OS X: You are running Mountain Lion (10.8) or later, and only purchase and run programs from the Apple App store.
This is such an important issue that I submitted a vulnerability report to CERT. It’s a long post, but I encourage you to take the time to understand it. It’s at the heart of many other security issues that I’ve written about on this blog. Also, make sure you read my follow-up post, How to Protect Your Quicken Data from All Your Programs.
Suppose you are running a program where you enter (and store) sensitive financial data (I chose “Quicken 2002 Deluxe” as an example program). And, also suppose that you like to cook, so you download and install a recipe program (I choose “Living Cookbook 2013” as an example program).
Note: I am not trying to pick on Quicken 2002 Deluxe and Living Cookbook 2013. They are just the example programs I chose. Any other Windows program that you install would have the same issue.
When you login to your PC, you login as your user. Let’s say your user name is “John Smith”. OK, John. Login to your PC. Once you have logged in, you can see your user name is “John Smith”:
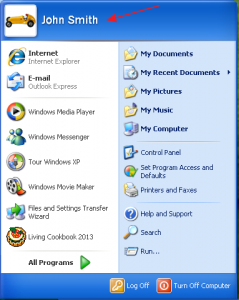
Note: If you have trouble seeing the images, click on them to make them bigger. Then click on the browser’s Back button to come back to the article.
When you run your Quicken program, it will be running as user “John Smith”. You can see this in the Task manager:
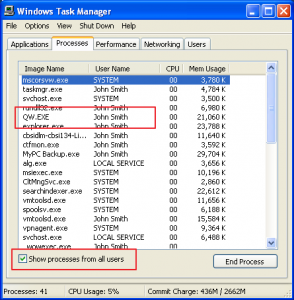
You can see that your Quicken program (QW.EXE) is running as user “John Smith”. Let’s take a look at your Quicken Program:
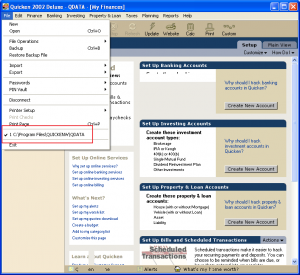
If you click on “File” to see the pull-down menu, you can see what file Quicken is using to store your financial data:
C:\Program Files\QUICKENW\QDATA
Let’s go look at the data file created by Quicken:
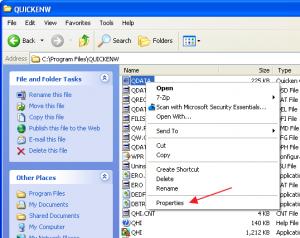
If you navigate to the C:\Program Files\QUICKEN directory, and do a right-click on the QDATA file, click on Properties, then click the Security tab:
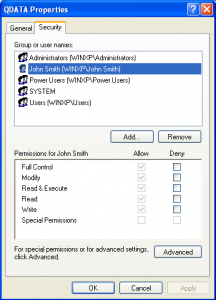
So, for the QDATA file, a person logged in as “John Smith” has these permissions:
Full Control
Modify
Read & Execute
Read
Write
OK, are you with me so far?
Now, let’s run the recipe program.
And, then run Task Manager again:
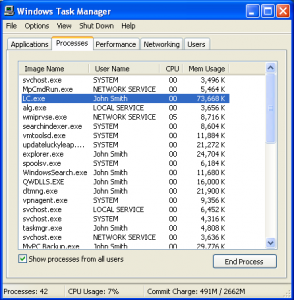
You can see that Living Cookbook 2013 is running as user “John Smith”. This means that it has FULL CONTROL over your Quicken data file.
Huh? OK, let’s think about this: When the Living Cookbook 2013 program is running, what user is it running as? John Smith
What permissions does the user John Smith have on your Quicken data file? Full Control.
What does FULL CONTROL mean? It means the Living Cookbook 2013 program can read your Quicken data file, it can overwrite your Quicken data file, and/or it can delete your Quicken data file.
To fully understand the scope of this, it means that ANY program you run while you are logged in as “John Smith” has FULL CONTROL over your Quicken data file QDATA. It can read it, modify it, and/or delete it. If it wants to, it can send your Quicken data file over the Internet to a hacker site HACKERS_R_US.COM, and the hackers could look at your financial data. If you did online banking, and you store your banking passwords in Quicken, the hackers might be able to extract your banking passwords too.
Actually, it is worse than that. It applies to any program you run while you are logged in as “John Smith”. Quicken can obliterate your recipes, Skype can erase your Word docs, AOL Messenger can destroy your spreadsheets, and your cool new download can send ALL your files to HACKERS_R_US.COM. The main message is that, if you are logged in as the same user (which is what most of us do on our personal computers), there is no inter-application security at all.
That is how the Windows security model works.
Now even though the examples are from Windows XP, the Mac OS X security model works the same way, so:
That is how the Mac OS X security model works.
I have spent years working on Linux and Unix, so I can say with certainty:
That is how the Linux and Unix security models work.
Now, if all programmers played by the rules, and restricted themselves to data files maintained by their own program, this wouldn’t be a problem. However, you have no guarantee of that, and the current security models don’t help you protect your data. If you install and run any malicious programs that don’t play by the rules, all bets are off.
Now, I raised this issue to the Microsoft Security Response Center. It took a few back and forth emails to fully explain my concern. When the Microsoft Security Response Center understood my concern, here is the response I got:
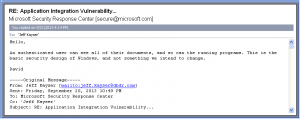
An authenticated user can see all of their documents, and so can the running programs. This is the basic security design of Windows, and not something we intend to change.
I expect that this is true of both the server and desktop versions of Windows. I hope the the answer is a little more nuanced with some of the newer security features.
Sorry to be the bearer of bad news, but it is what it is. My goal is to educate, so that people know the risks, and can make informed decisions about what to do to protect their data.
To learn what you can do to protect your sensitive data, read How to Protect Your Quicken Data from All Your Programs.
|
|
















Recent Comments