Note: The issue discussed on this page affects you if you use Windows or Mac OS X, unless you have taken the following precautions:
- For Windows: You are running Windows 8 or later, and only purchase and run programs from the Windows App store.
- For Mac OS X: You are running Mountain Lion (10.8) or later, and only purchase and run programs from the Apple App store.
This is such an important issue that I submitted a vulnerability report to CERT. It’s a long post, but I encourage you to take the time to understand it. It’s at the heart of many other security issues that I’ve written about on this blog. Also, make sure you read my follow-up post, How to Protect Your Quicken Data from All Your Programs.
Suppose you are running a program where you enter (and store) sensitive financial data (I chose “Quicken 2002 Deluxe” as an example program). And, also suppose that you like to cook, so you download and install a recipe program (I choose “Living Cookbook 2013” as an example program).
Note: I am not trying to pick on Quicken 2002 Deluxe and Living Cookbook 2013. They are just the example programs I chose. Any other Windows program that you install would have the same issue.
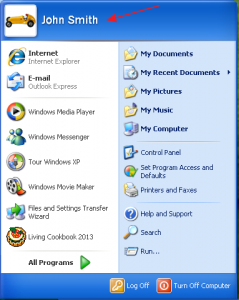
When you login to your PC, you login as your user. Let’s say your user name is “John Smith”. OK, John. Login to your PC. Once you have logged in, you can see your user name is “John Smith”:
Note: If you have trouble seeing the images, click on them to make them bigger. Then click on the browser’s Back button to come back to the article.
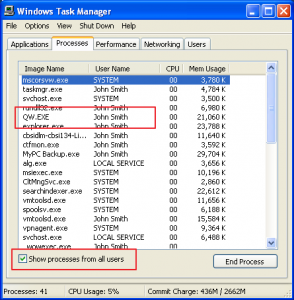
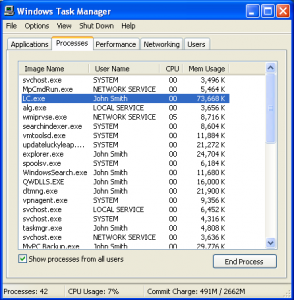
When you run your Quicken program, it will be running as user “John Smith”. You can see this in the Task manager:
You can see that your Quicken program (QW.EXE) is running as user “John Smith”. Let’s take a look at your Quicken Program:
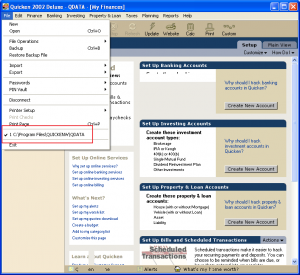
If you click on “File” to see the pull-down menu, you can see what file Quicken is using to store your financial data:
C:\Program Files\QUICKENW\QDATA
Let’s go look at the data file created by Quicken:
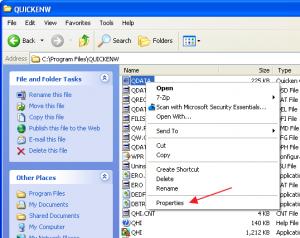
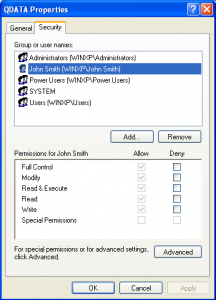
If you navigate to the C:\Program Files\QUICKEN directory, and do a right-click on the QDATA file, click on Properties, then click the Security tab:
So, for the QDATA file, a person logged in as “John Smith” has these permissions:
Full Control
Modify
Read & Execute
Read
Write
OK, are you with me so far?
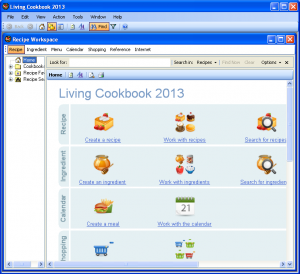
Now, let’s run the recipe program.
And, then run Task Manager again:
You can see that Living Cookbook 2013 is running as user “John Smith”. This means that it has FULL CONTROL over your Quicken data file.
Huh? OK, let’s think about this: When the Living Cookbook 2013 program is running, what user is it running as? John Smith
What permissions does the user John Smith have on your Quicken data file? Full Control.
What does FULL CONTROL mean? It means the Living Cookbook 2013 program can read your Quicken data file, it can overwrite your Quicken data file, and/or it can delete your Quicken data file.
To fully understand the scope of this, it means that ANY program you run while you are logged in as “John Smith” has FULL CONTROL over your Quicken data file QDATA. It can read it, modify it, and/or delete it. If it wants to, it can send your Quicken data file over the Internet to a hacker site HACKERS_R_US.COM, and the hackers could look at your financial data. If you did online banking, and you store your banking passwords in Quicken, the hackers might be able to extract your banking passwords too.
Actually, it is worse than that. It applies to any program you run while you are logged in as “John Smith”. Quicken can obliterate your recipes, Skype can erase your Word docs, AOL Messenger can destroy your spreadsheets, and your cool new download can send ALL your files to HACKERS_R_US.COM. The main message is that, if you are logged in as the same user (which is what most of us do on our personal computers), there is no inter-application security at all.
That is how the Windows security model works.
Now even though the examples are from Windows XP, the Mac OS X security model works the same way, so:
That is how the Mac OS X security model works.
I have spent years working on Linux and Unix, so I can say with certainty:
That is how the Linux and Unix security models work.
Now, if all programmers played by the rules, and restricted themselves to data files maintained by their own program, this wouldn’t be a problem. However, you have no guarantee of that, and the current security models don’t help you protect your data. If you install and run any malicious programs that don’t play by the rules, all bets are off.
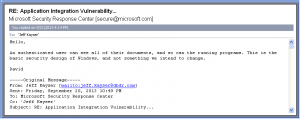
Now, I raised this issue to the Microsoft Security Response Center. It took a few back and forth emails to fully explain my concern. When the Microsoft Security Response Center understood my concern, here is the response I got:
An authenticated user can see all of their documents, and so can the running programs. This is the basic security design of Windows, and not something we intend to change.
I expect that this is true of both the server and desktop versions of Windows. I hope the the answer is a little more nuanced with some of the newer security features.
Sorry to be the bearer of bad news, but it is what it is. My goal is to educate, so that people know the risks, and can make informed decisions about what to do to protect their data.
To learn what you can do to protect your sensitive data, read How to Protect Your Quicken Data from All Your Programs.

Recent Comments